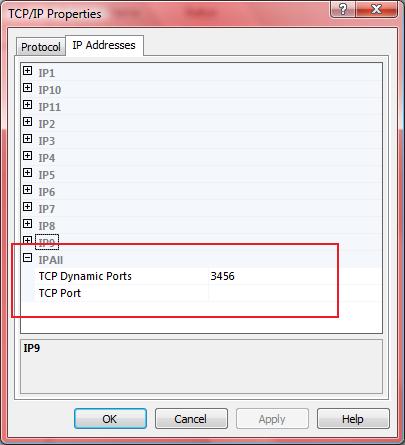
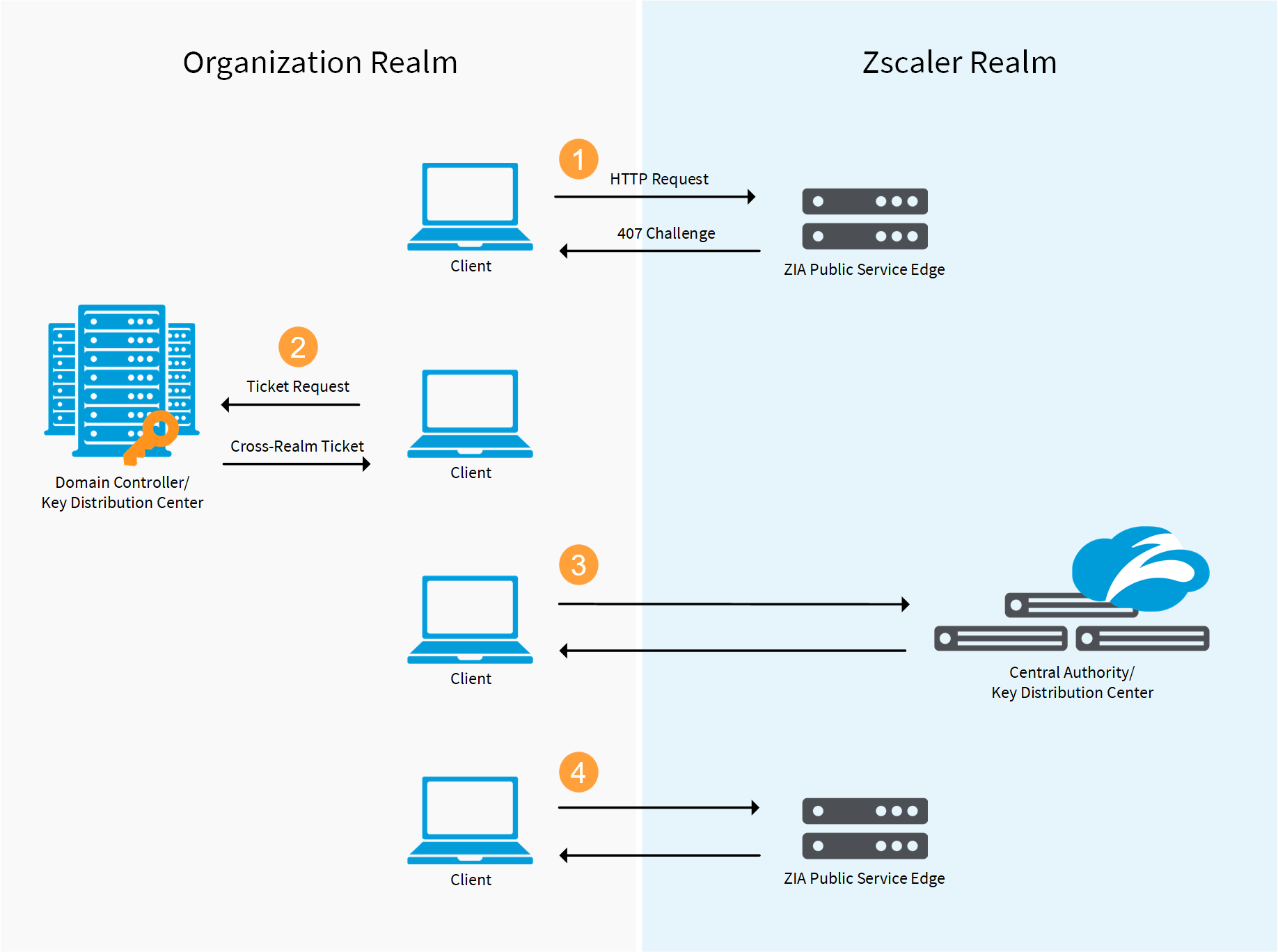
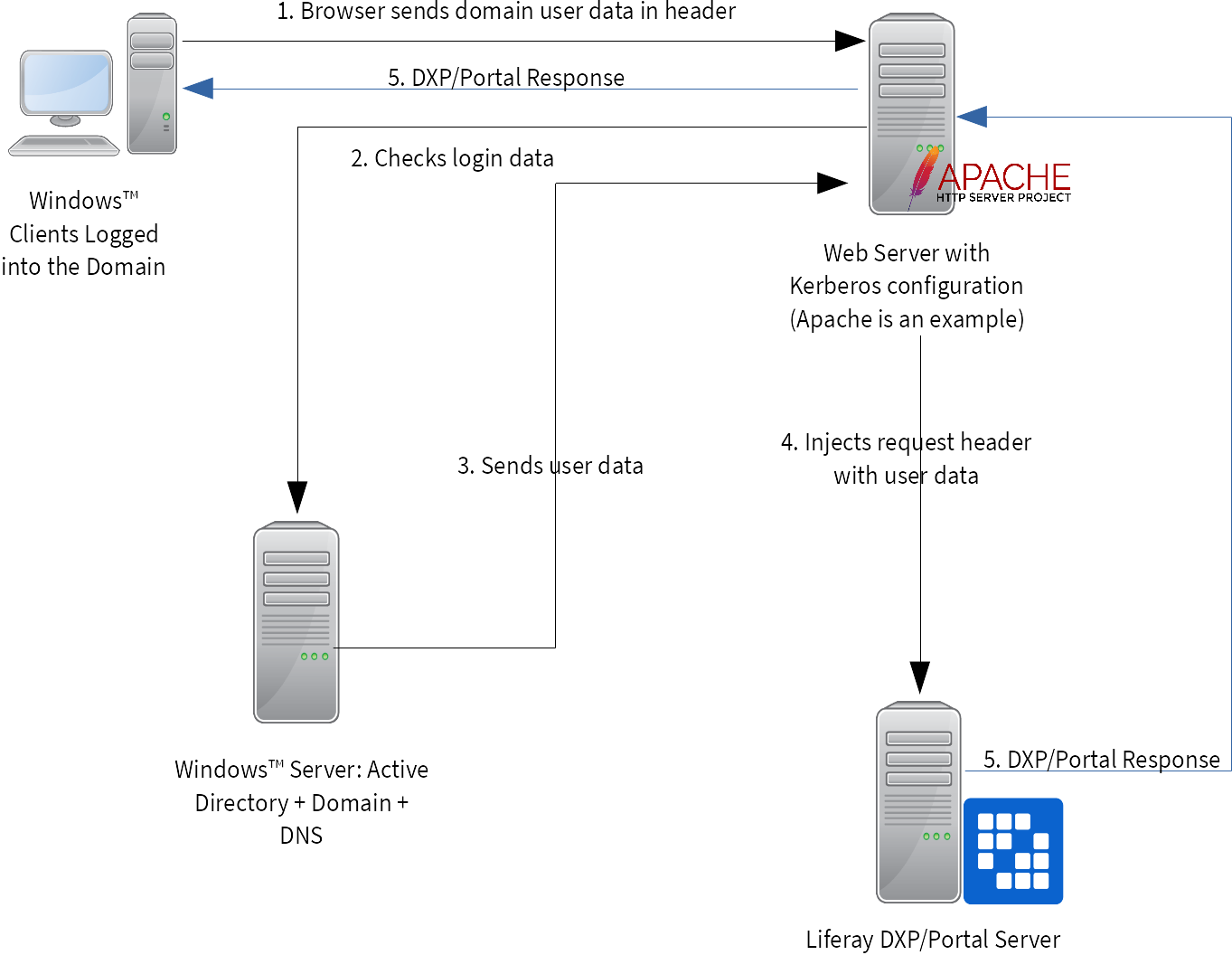
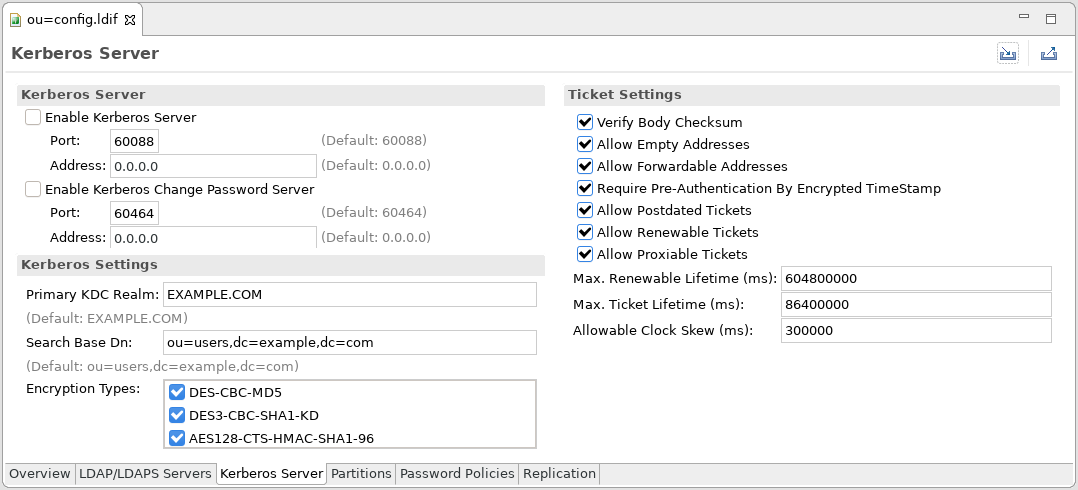
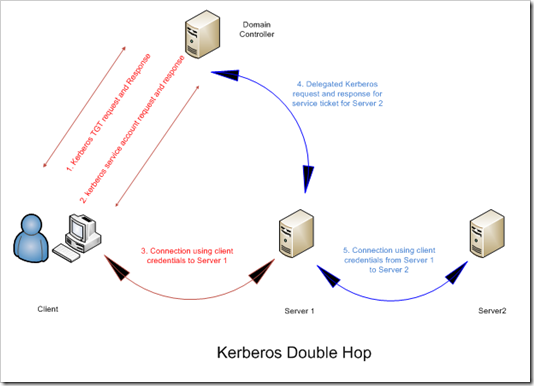
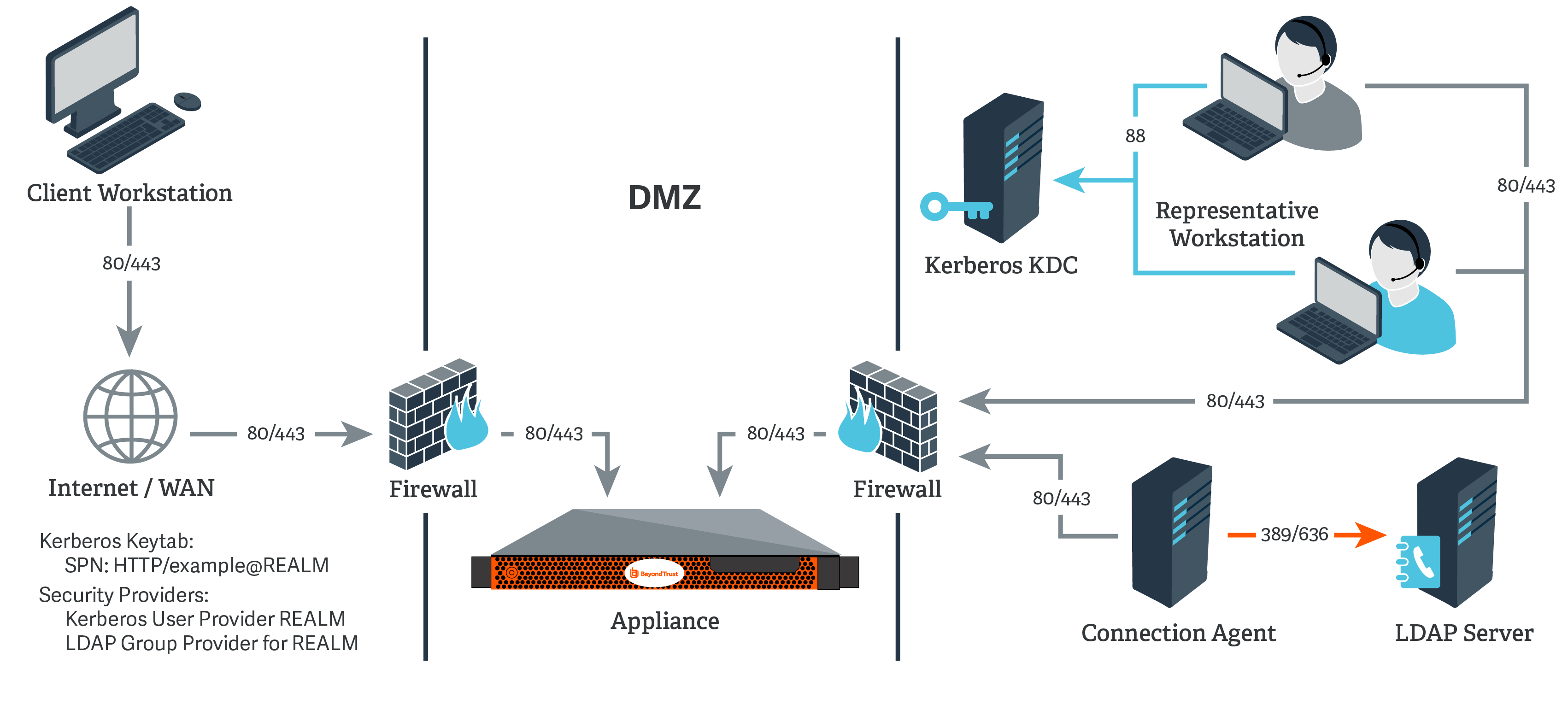
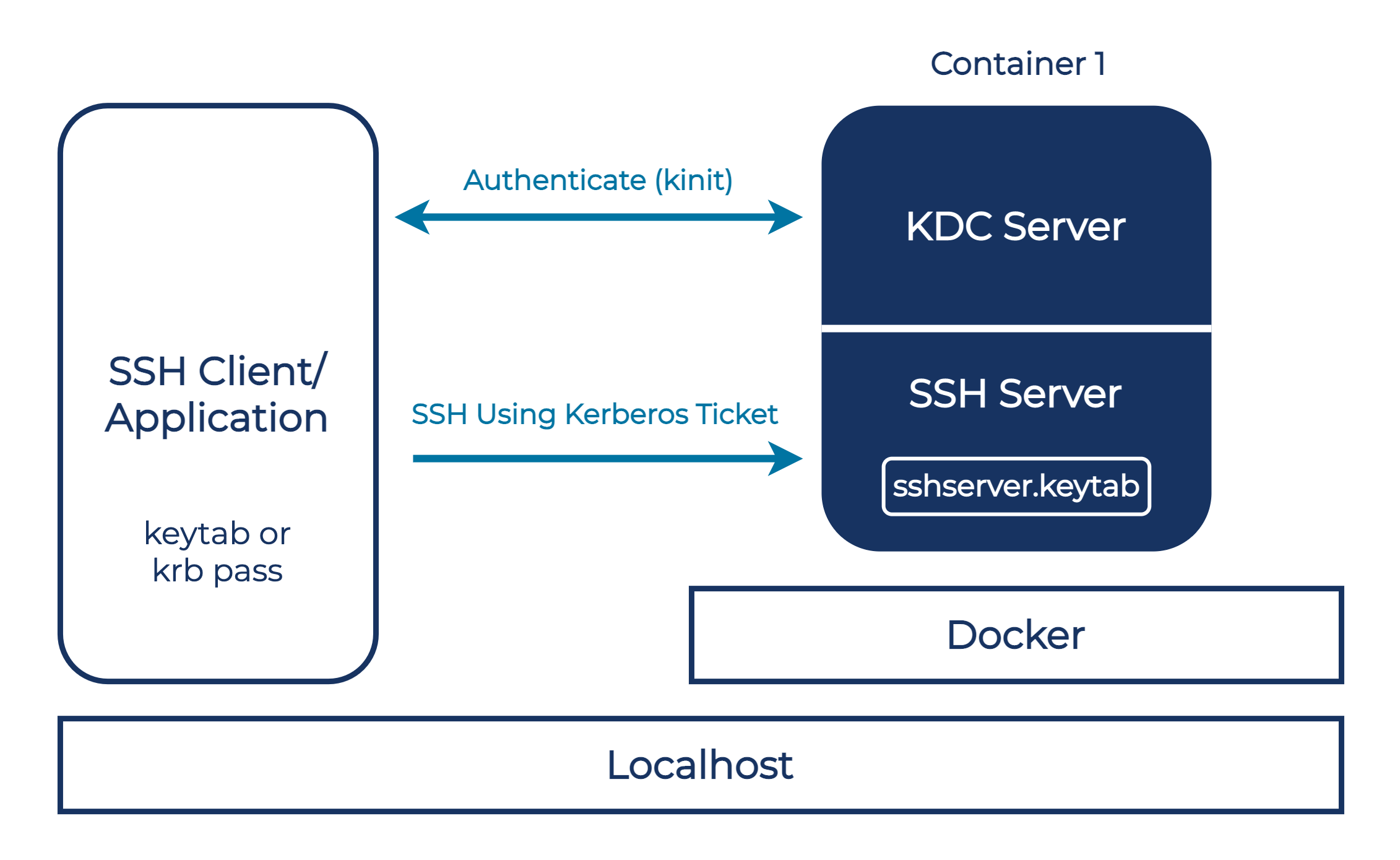
Enabling Kerberos authentication - Asset Reliability | AssetWise APM Wiki - Asset Reliability | AssetWise APM - Bentley Communities
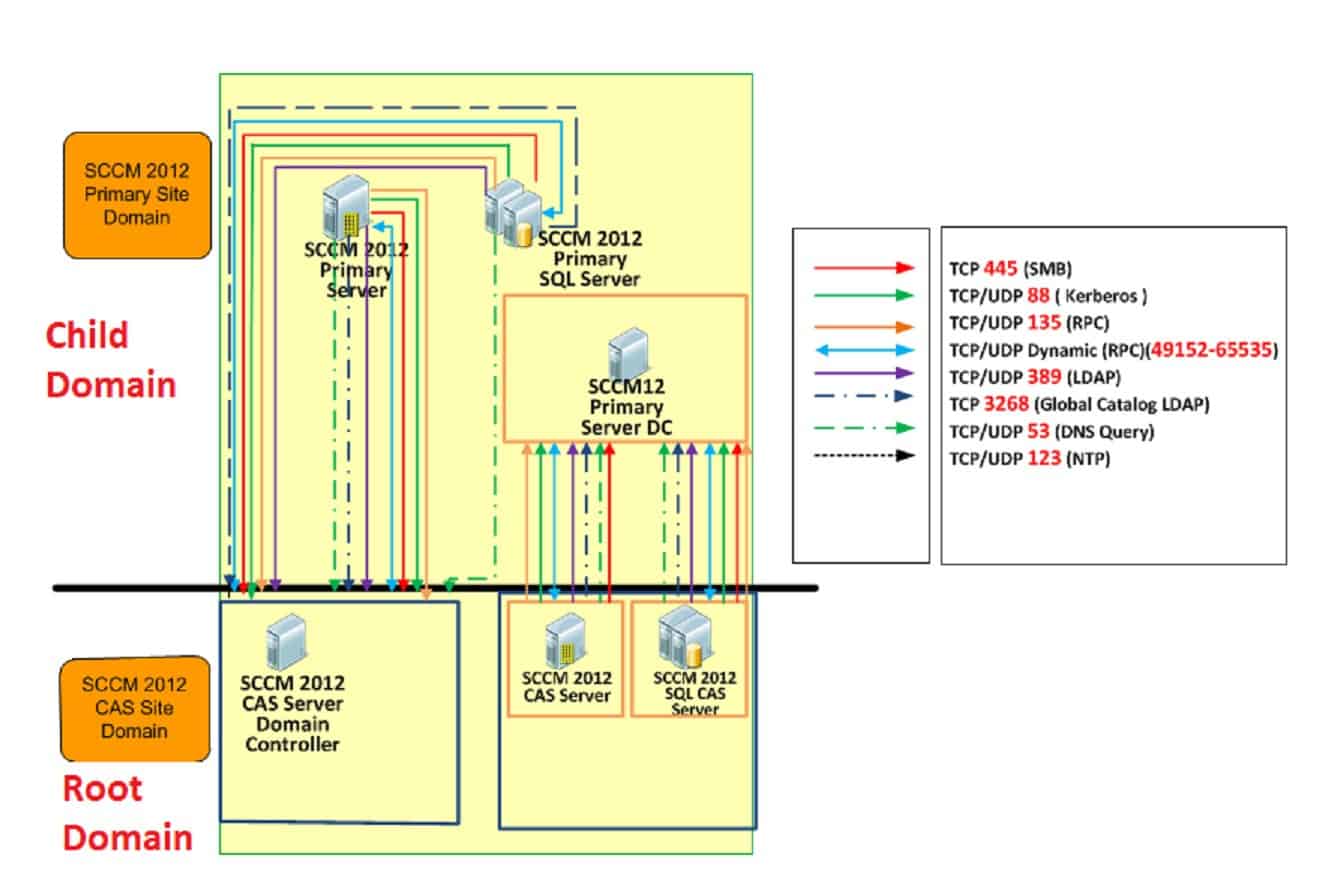
SCCM Firewall Ports Details Direction With DC Other Servers | Configuration Manager | Bi-direction HTMD Blog




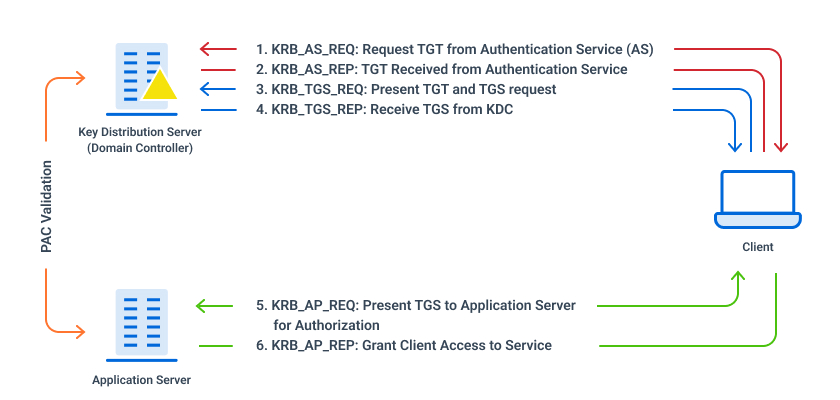

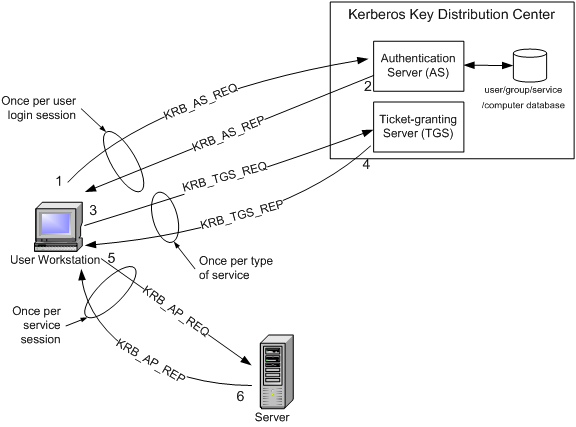
![Firewalls, NAT, and Kerberos - Kerberos: The Definitive Guide [Book] Firewalls, NAT, and Kerberos - Kerberos: The Definitive Guide [Book]](https://www.oreilly.com/api/v2/epubs/0596004036/files/httpatomoreillycomsourceoreillyimages2077824.png)